-
16 Aug 2017
Hacking For Dummies featured in new Lifetime movie Running Away
I had the neat opportunity to recently see my book, Hacking For Dummies, featured in this summer's Lifetime movie called Running Away. I've known that it was a possibility for some time but it was cool to see it on the screen! Here's the scene it's featured in:You can see more about - and purchase - Hacking For Dummies (currently in its 5th edition) on Amazon by clicking the graphic ...
Continue Reading... -
10 Aug 2017
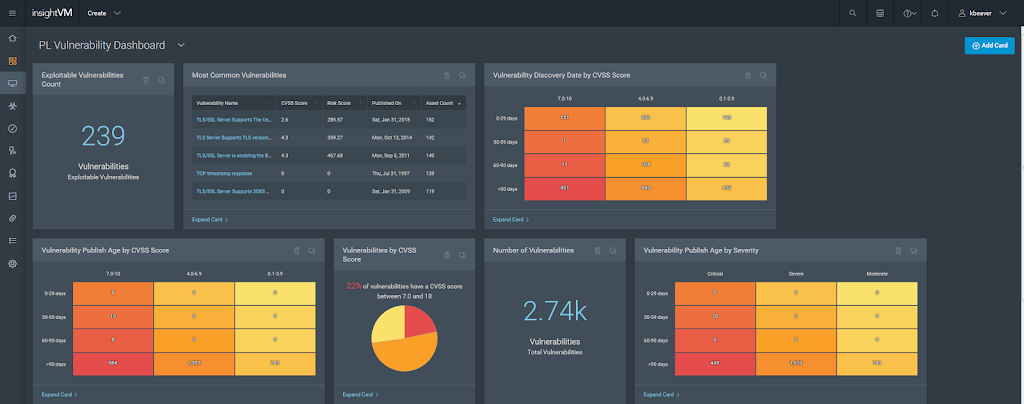
Rapid7’s Insight platform provides focused analytics for your security program
Fairly recently, Rapid7 took their vulnerability management platform up to the next level with their analytics platform called Rapid7 Insight. It's a beneficial for an independent consultant like myself and even more useful for enterprises with IT environments of growing complexity. Rapid7 Insight is marketed as a way to bring together the Nexpose vulnerability research, Metasploit exploits, global security intelligence and exposure analytics into a single system that can help ...
Continue Reading... -
07 Aug 2017
How to gain control & become an IoT security expert
You've no doubt heard the vendor spiels and seen their solutions for gaining control of your Internet of Things environment. But do you truly have IoT under control? Like other things in IT, it can be pretty overwhelming, especially when you're struggling to keep your arms around your traditional network environment with cloud and mobile and all the complexities they bring. Well, IoT security doesn't have to be that difficult. It's ...
Continue Reading... -
21 Jun 2017
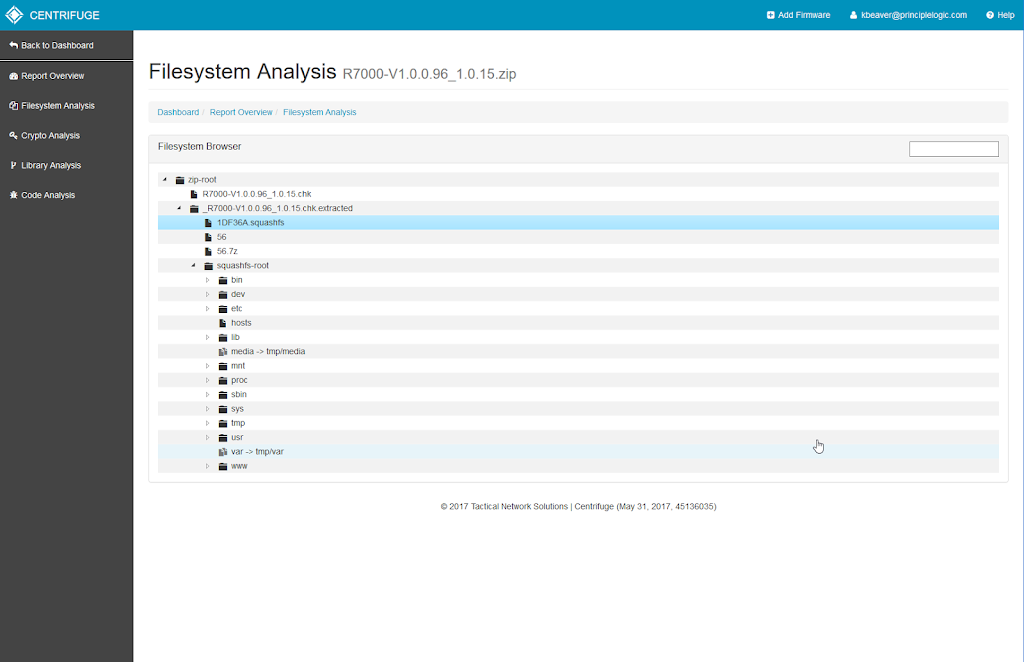
Using Centrifuge for IoT security testing
I love hacking things, especially new things like what's showing up on networks around the globe in the form of IoT. If IoT security is anywhere on your radar, you're likely incorporating these devices into your security testing program. Well, there's a new IoT security assessment tool in town that you need to know about called Centrifuge brought to you by Tactical Network Solutions - makers of the former (and ...
Continue Reading... -
26 May 2017
From web to mobile to connected cars – here are some application security resources you need to check out
Given all of the variables and complexities associated with information security, I still believe that application security is the biggest weakness in most organizations and the one area where we can truly effect the greatest change. Here are some pieces that I have written recently regarding web and mobile app security that you might enjoy:Identifying and addressing overlooked web security vulnerabilitiesWhat the end of hot patching mobile apps means for ...
Continue Reading... -
17 May 2017
My new content on preventing ransomware + infosec leadership and careers
From ransomware to IT and security leadership and careers - they all sort of go hand-in-hand. Here's some new content for you to check out: Five ways to prevent a ransomware infection through network security An unfunded mandate is not a mandate How top IT pros stand apart Using unrealized IT talent to your advantage Great ways to get management on your side with application security The side-effects of miscommunication ...
Continue Reading... -
15 May 2017
The real reasons behind the WannaCry ransomware
As we continue down the path of yet another major security breach - this time with the ransomware WannaCry - let us remember that it's not just about the criminal hackers, out-of-control government agencies such as the NSA, or vendors such as Microsoft putting out vulnerable software. Every single one of us working in IT, security, and business today are complicit in these challenges. Outdated/unsupported operating systems are running. We ...
Continue Reading... -
08 May 2017
My CSO interview/story: What it takes to be an independent information security consultant
I'm very honored to have been interviewed recently for CSO Magazine about my background and what it takes to stand out - and survive - as an independent security consultant. Check it out here:Thanks for the nice write-up, Bob Violino!...
Continue Reading... -
01 May 2017
Thoughts on the 2017 Verizon DBIR, hacking security policies, breaking into the infosec field, ransomware and more
Here are some recent pieces I've written for the good people at IANS: Verizon DBIR shows why we’re still struggling with security Security policies don’t get hacked. Why do they get all the attention? Strategies for Thwarting State-Sponsored Hacks Rooting out Ransomware Where, exactly, is your information? CEO Spoofing - Don't get fooled Take responsibility for vendor product security Are you making this mistake with your phishing awareness campaign? As ...
Continue Reading... -
13 Apr 2017
Why SOC audit reports can be misleading, mobile app security gotchas, and more…
Here are some links to recent articles I've written regarding application security...if you take anything away from this, it's that you can't afford to take this part of your security program lightly. Dealing with vendors who want to push their SOC audit reports on you Explaining discrepancies in different security assessment reports Why DAST and SAST are necessary if software is solid from the get-go Nixing credential re-use across unrelated ...
Continue Reading...