-
30 Aug 2019
SQL injection is lurking…Are you looking for it?
I don't always find SQL injection vulnerabilities in the web applications I test but I have been seeing it more and more recently. I can't figure out why... When I do uncover this grandest of all vulnerabilities, it's usually pretty ugly as it was with this recent finding: Using Acunetix Web Vulnerability Scanner to uncover SQL injection across various web pages and parameters Look for this flaw. Use good tools ...
Continue Reading... -
13 Jul 2018
Introducing my brand new vulnerability and penetration testing book: Hacking For Dummies, 6th edition
Want to learn the essentials of vulnerability and penetration testing? Looking for insight into which testing tools you need to use to get the job done right? Maybe you need help in determining the difference between the vital few security vulnerabilities and the trivial many that sidetrack so many people? Perhaps you need help selling information security to management and keeping them on board with what you're doing? Well, if ...
Continue Reading... -
21 Dec 2017
Web application and mobile app security testing – Are you on board?
Here are some recent pieces I've written regarding web application and mobile app security based on the work I do that you might be interested in: How security controls affect web security assessment resultsThe importance of integrating mobile apps into your security programHow automated web vulnerability scanners introduce risksAddressing web server security vulnerabilities below the application layerDon’t sweep web application testing under the rugYou may not be in control but ...
Continue Reading... -
07 Aug 2017
How to gain control & become an IoT security expert
You've no doubt heard the vendor spiels and seen their solutions for gaining control of your Internet of Things environment. But do you truly have IoT under control? Like other things in IT, it can be pretty overwhelming, especially when you're struggling to keep your arms around your traditional network environment with cloud and mobile and all the complexities they bring. Well, IoT security doesn't have to be that difficult. It's ...
Continue Reading... -
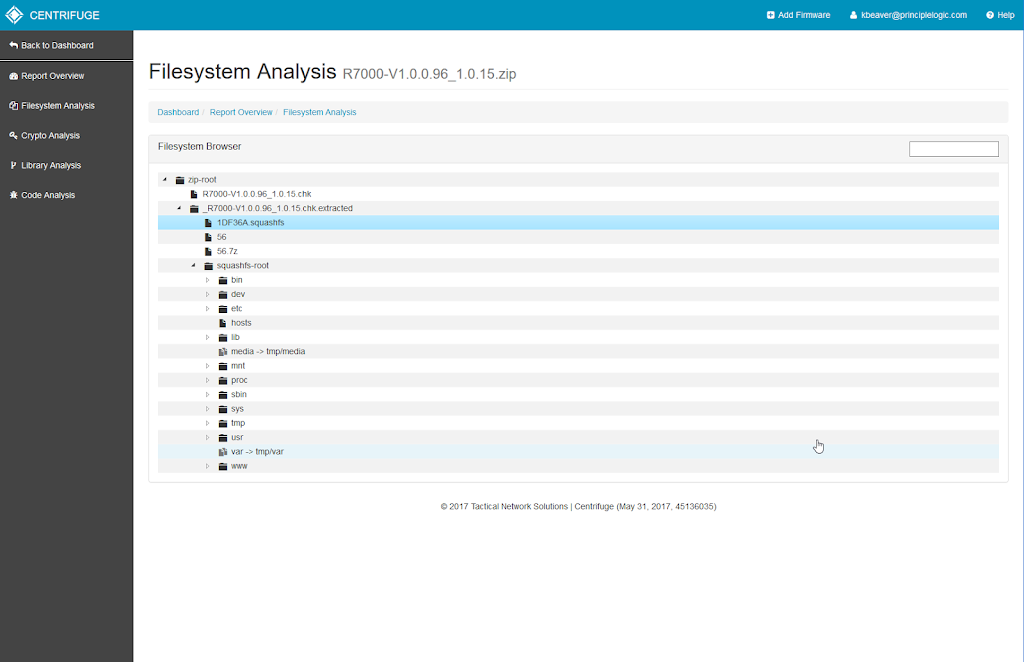
21 Jun 2017
Using Centrifuge for IoT security testing
I love hacking things, especially new things like what's showing up on networks around the globe in the form of IoT. If IoT security is anywhere on your radar, you're likely incorporating these devices into your security testing program. Well, there's a new IoT security assessment tool in town that you need to know about called Centrifuge brought to you by Tactical Network Solutions - makers of the former (and ...
Continue Reading... -
31 Mar 2017
Outsourcing security monitoring, guest wireless network risks, and more infosec content to help your business
I can't believe that I recently submitted my 1,000th article...it's been a long time coming! I first started writing in 2001 and it has been one of the best things I ever did. Thanks so much for your support over the years!Here's some new content I've written for the nice folks over at Toolbox.com (Ziff Davis) that you might be interested in: Outsource your security monitoring/alerting and be done with ...
Continue Reading... -
05 Dec 2016
Using NowSecure for automated mobile app testing
As an independent information security consultant, I'm always looking for good testing tools to rely on for my work. These tools, such as vulnerability scanners, network analyzers/proxies, and related manual analysis tools, are not the be-all-end-all answer for uncovering security weaknesses, but they are a very important aspect of what I do. Be it more generic vulnerability scans, a targeted penetration test, or a broader, more in-depth, security assessment, I ...
Continue Reading... -
12 Aug 2016
Penetration Testing and Security Assessment Essentials…Don’t ignore this stuff.
Want tips on how to perform better security assessments and penetration tests? Here you go:What are the most important security testing basics?Determining your scope of security testingBest Practices and Tips for Choosing Application Security Testing ToolsWhy ALL of your Web applications need security testingIt can be dangerous assuming a vulnerability is not a vulnerabilityWhat constitutes a “critical” security flaw?Rely on data center audits alone and you’ll get hit eventually What ...
Continue Reading... -
28 Jun 2016
Email phishing expertise: Lack of skills or just a lackadaisical approach to security?
I can't think of any current security test that's more important than email phishing. Yet, it seems that so few organizations actually include this phishing as part of their ongoing information security assessments and penetration tests. I suppose that's why we keep hearing about all of the Cryptolocker infections and crazy statistics being published by Verizon, Ponemon and others. Here are some articles that I have written that can help ...
Continue Reading... -
25 Apr 2016
New content on web application security testing
Here are a two brand new pieces I've written on web application security recently for the nice folks at TechBeacon:Why ALL of your apps need security testing4 insider tips for choosing application security testing toolsMore to come - you can link/subscribe to my author page here. Enjoy!...
Continue Reading...