-

WebInspect: How SQL injection testing *should* be done
17 Dec 2011SQL injection is arguably the grandest of all security vulnerabilities. It can be exploited anonymously over the Internet to gain full access to sensitive information – and no one will ever know it occurred. Yet time and again it’s either:
- overlooked by people who don’t test all of their critical systems from every possible angle
- overlooked by people who haven’t learned how to properly use their Web vulnerability scanners
- overlooked by people who chose to only perform PCI-DSS-type vulnerability scans that don’t go deeply enough
- And, perhaps worst of all, overlooked by tools that can’t test for – or properly exploit – SQL injection
Certain automated tools for SQL injection testing/exploitation have been around for years but I’ve never seen a tool that actually finds SQL injection as frequently or is as simple to use as HP’s WebInspect. As shown in the following screenshots, with WebInspect it’s a simple two-step process from initial scan to data extraction:
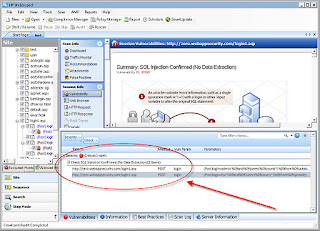 Step 1: Run the vulnerability scan to find SQL injection flaws. Finding it is half the battle. Most vulnerability scanners have no clue of its existence.
Step 1: Run the vulnerability scan to find SQL injection flaws. Finding it is half the battle. Most vulnerability scanners have no clue of its existence. Step 2: Right-click on the finding, load the SQL Injector tool to confirm the injection and then click Pump Data to automatically siphon data out. Yes, it’s that simple. (Note: in this test instance, extraction was not possible but it is in at least half of the SQL injection flaws I come across).
Step 2: Right-click on the finding, load the SQL Injector tool to confirm the injection and then click Pump Data to automatically siphon data out. Yes, it’s that simple. (Note: in this test instance, extraction was not possible but it is in at least half of the SQL injection flaws I come across).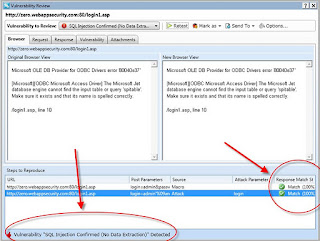 At your option, you can also use WebInspect’s Vulnerability Review function to go back and test the SQL injection flaws once a fix is put in place…no need for a full rescan. Love it.
At your option, you can also use WebInspect’s Vulnerability Review function to go back and test the SQL injection flaws once a fix is put in place…no need for a full rescan. Love it.Folks, this is something that cannot be taken lightly. I’m not just talking about SQL injection itself but the fact that your tools may not be providing you the right information you need. As I’ve said before, You cannot secure what you don’t acknowledge. In this case, I’ll tweak that a bit and say You cannot secure what you cannot find. Just because the tools you’re using aren’t finding or exploiting SQL injection doesn’t mean it’s not a problem. Trust but verify.



