-

What you need to know about Checkmarx CxSAST version 8
20 Apr 2016Application security tool version upgrade usually don’t excite me as it’s often the same old, same old with a few new checks and niche features. However, the new version of Checkmarx CxSAST (formerly CxSuite, CxDeveloper, etc.) is spot-on. The next generation of the popular static source code analyzer – version 8 – was recently released and it contains some much-needed improvements over its predecessor.One thing that’s glaringly evident in version 8 is the streamlined installation process. Minimal options. No tricky questions. No random services installed to junk up your system (at least that I know of). It just installs and is ready to use in less than 5 minutes. I installed CxSAST on a much less powerful virtual machine than I had version 7 running on and it actually seems to be much faster. I’m not sure if this was by design or if it’s just something in my head but it’s a nice new feature. Additional features in version 8 (currently 8.0.1) that I think are beneficial include:
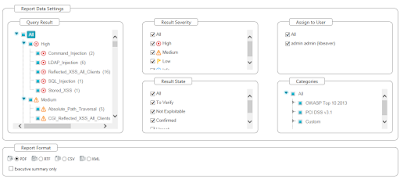
- Major overhaul in the user interface – it was a long-time coming and it’s lot better/easier. Here’s a sample screenshot:
- A new vulnerability state option of “Proposed Not Exploitable” for findings that are likely non-issues (you get quite a few of these when performing a source code analysis)
- I haven’t yet tried it (but suspect I will as my testing environment changes often) – apparently the CxSAST engine can now be deployed without enforcing the Hardware ID for the license. Nice.
- Incremental (partial) scans can now be run via the native IDEs in Eclipse, IntelliJ, and Visual Studio
Checkmarx CxSAST has as much language support than other products I’m familiar with by supporting the traditional languages (C#, Java, VB.Net, PHP) as well as Ruby, Objective C, JavaScript, etc. To me, the mobile app support for Android and iOS is one of its biggest selling points.
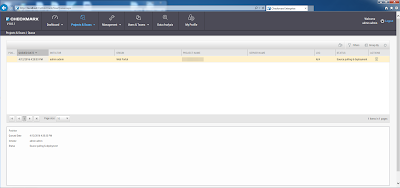
I’m seeing an uptick in source code analysis interest. Perhaps it’s because people are realizing that web vulnerability scanners and manual analysis simply can’t find it all. Regardless, if you’re looking to integrate source code analysis into your SDLC or do some last-mile security checks on enterprise web applications, mobile apps, or even legacy client/server applications, Checkmarx CxDeveloper, I mean CxSAST, needs to be on your radar. Here’s a screenshot of some sample findings from the tool after scanning a Java application – many of which were not uncovered during traditional web vulnerability testing:
By the way, in the event you’re looking to brush up on your application security skills, Checkmarx’s Vulnerability Knowledgebase is a good resource for details on various application security vulnerabilities.