-

Experiencing problems with authenticated web vulnerability scans? Try NTOSpider.
07 Oct 2013You’re performing authenticated web vulnerability scans, right? If you’re not, you’re missing out…big time.
When performing authenticated scans, you’ll find a whole different set of security flaws likely consisting of session fixation, SQL injection (that often differs among user role levels), weak passwords, login mechanism flaws, and perhaps…just maybe that beloved cross-site request forgery flaw that may or may not be exploitable or even matter in the context of what you’re doing.
Bottom line: you need to be testing for flaws behind your web login prompts.
The thing is, though, authenticated web vulnerability scanning can extremely painful and inaccurate at best. If you’re not paying attention, your web vulnerability scanner is not going to authenticate properly, it’s not going to stay logged in, it’s going to continually lock the user account (a major annoyance), or it’s not going to properly crawl the entire application. Many of these pains are doubly true if your web applications are using Web 2.0 technologies (can we still call them that?).
Web vulnerability scanners are getting better and better, but the problems with authenticated web vulnerability scans still exist with most scanners I’ve tried – at least some of the time. Except one…NTObjectives’ NTOSpider.
I’ve written about NTOSpider before (here and here) and in the interest of helping out my fellow IT/security professionals who are performing authenticated web vulnerability scans and experiencing these same pains, I feel I have to say something about NTOSpider again…
Check it out. It works extremely well with authenticated scans. Whatever Dan Kuykendall and his guys are doing to get the tool to establish and maintain state – for the entire scan, without locking up, or taking two weeks to run – it’s working. Kudos.
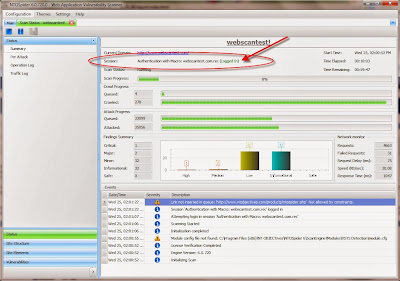
One of the neatest things about NTOSpider is that it will tell you whether or not the scanner is logged in as you can see in the screenshot below:
It’s a brilliant feature – something I haven’t yet seen on any other web vulnerability scanner. I’m sure some people don’t value such a feature (think: “Let’s just get this scan done, check our box, and move on!”) but it’s very useful if you want to make sure your authenticated scans are running properly.
NTOSpider definitely won’t find every web security flaw. I haven’t yet found a scanner that will. With enough experience, you’ll see that this is one of the fundamental problems we have with web vulnerability testing. Relying on a single web vulnerability scanner to find all the flaws is like relying on a single firewall to keep every threat out of your network. It’s not going to happen.
NTOSpider is not perfect either. It has several quirks – some of which have been resolved in the latest version 6 (which is much improved). But, again, I haven’t yet found a scanner that is perfect.
The only thing that matters is that NTOSpider feels perfect when it ends up getting you out of a bind like it has for me several times now in my web security vulnerability assessment work. Add it to your arsenal of multiple web vulnerability scanners. You won’t regret it.