-

A couple of neat things about WebInspect
30 Mar 2010If you’re into finding the Web security flaws that matter HP’s WebInspect should be on your short list of prospective Web vulnerability scanners. Over the past six months WebInspect has repeatedly found a couple of items that I know I otherwise wouldn’t have uncovered or been able to exploit to the extent I did.
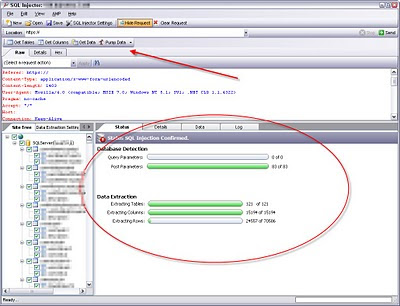
The first is SQL injection. WebInspect does a very good job finding the actual flawed inputs but really stands out when it comes to exploiting the vulnerabilities – something that proves highly valuable during security assessments. Recently, I came across an application that had authenticated SQL injection that was only exploitable at one role level – which was, of course, the unexpected one. The following is a screenshot of WebInspect’s SQL Injector in action showing it’s appropriately named “Data Pump” function.
You often have to tinker and be persistently patient with SQL Injector to get it to exploit a SQL injection flaw…and it does have its false-positive moments hence the need for detailed manual verification. But man, when it gets rolling, look out.
The second thing about WebInspect is its ability to uncover the usage of HTTP GET requests in an otherwise POST-centric world. As with SQL Injector, some are false positives so you have to manually verify that the finding is indeed a problem. But if you can confirm the issue your efforts will pay off because HTTP GET requests can “get” your users and your business in a real bind…It’s a big enough problem and such a common finding that it inspired me to write this article: Why use POST vs. GET to keep applications secure.
I could go on with more good things about WebInspect but I’ll save that for another time. Until then, don’t forget my firm belief that you almost always get what you pay for when it comes to Web vulnerability scanners…there’s just too much at stake not to invest in a good tool such as this.