-

Using Securolytics for enhanced IoT security
12 Sep 2018I often say that you can’t secure the things that you don’t acknowledge…I can’t imagine that reality applying to anything in IT or security as much as it applies to securing Internet of Things (IoT) devices that are on your network, creating risks…this very moment. The trouble with IoT devices that they can be not only hard to discover and manage but they’re also extremely difficult to identify. Oftentimes, in my vulnerability and penetration testing work, I come across IoT devices but much of it is a guessing game – especially when it comes to determining the specific manufacturer and what CVE or related vulnerabilities it might have. Traditional web and network vulnerability scanners are good at discovery and uncovering OS and application-related flaws but they lack the ability to dig in further and find out more information on the devices. That’s a problem…
Well, Atlanta, GA-based security vendor, Securolytics, has an answer to this common security management challenge. Their appliance/cloud service, which I’ve been evaluating over the past month, specializes in identifying IoT devices on your network so that they can be properly corralled, overseen and managed over the long haul. Securolytics specializes in the healthcare industry (where many IoT systems tend to reside), but the appliance and its software could work well in pretty much any environment. By analyzing network system behavior, DNS usage, syslog signatures and other “secret sauce” methods, the Securolytics system can identify some pretty unique IoT devices. For example, in my test network environment, it was able to identify some niche stuff such as a building automation device, a meeting room scheduling system, a consumer-based wireless access point, and, of all things that you wouldn’t want on your network, a cryptocurrency miner.
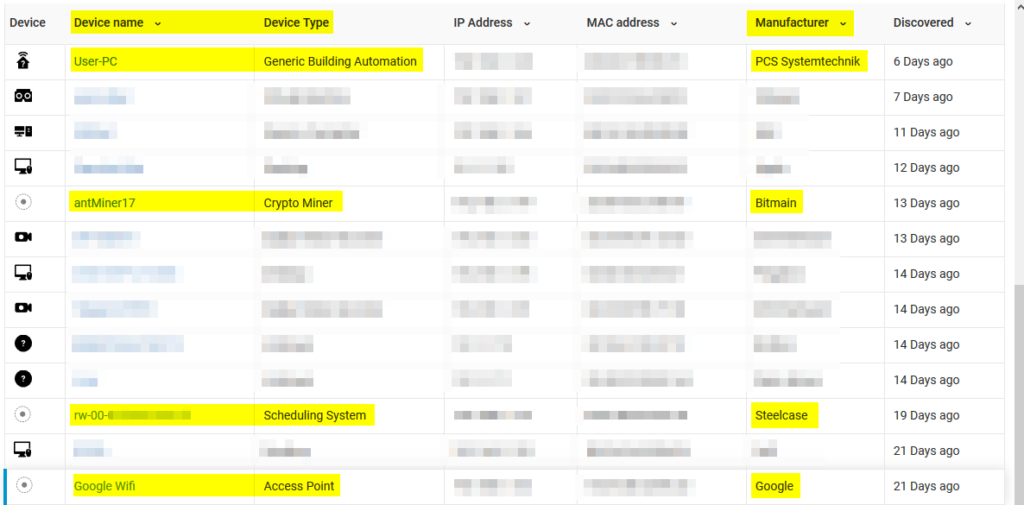
I have yet to see any other type of network tool be able to identify IoT systems so accurately.
Securolytics is great for mapping out an IoT footprint – especially for people like me performing security assessments – but it can also be used for IoT system monitoring, access control, threat defense and more – at an enterprise level. And it does this in a passive manner without local agents and without gathering or exposing sensitive information such as protected health information (PHI) under HIPAA.
The tool/product/service (I’m not sure what to call it!) can also perform an automated threat assessment that outlines confirmed or potential vulnerabilities in IoT devices:
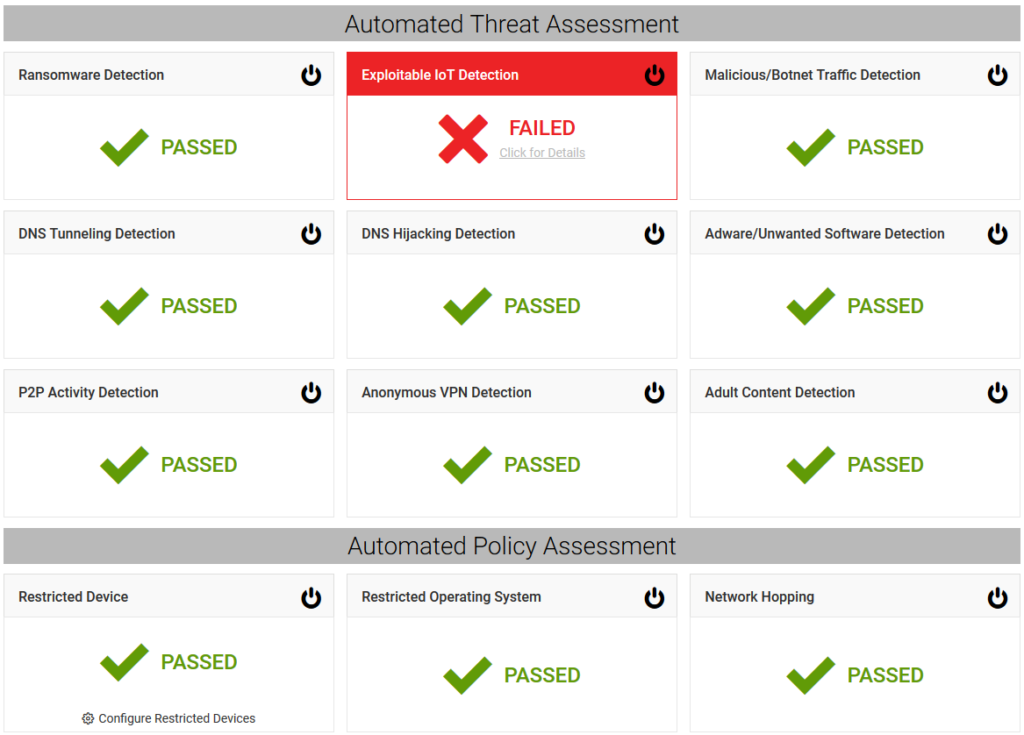
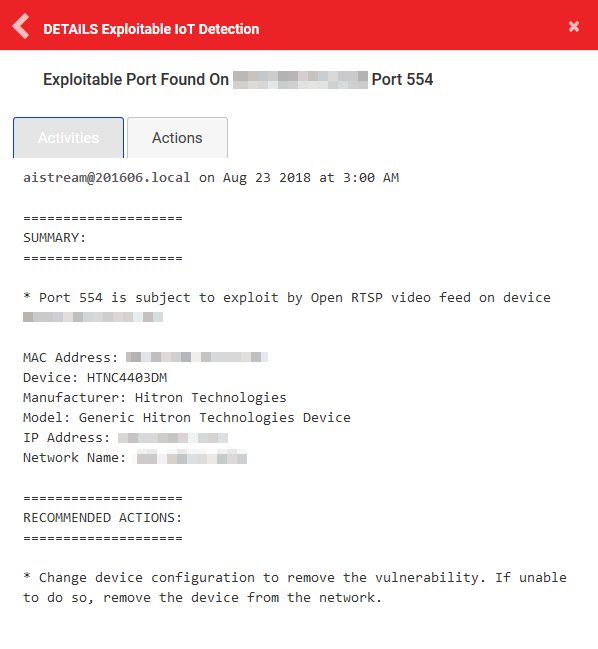
This is good for supplementing traditional port scanner and vulnerability scanner findings.
I’ve been working with clients (end users and the IoT manufacturers themselves) for several years to help identify business risks brought about by IoT devices. There’s a lot going on in the IoT security space and, if you work closely with these systems or simply need better insight into managing the ones that you know are on your network, you really need to check out Securolytics. It’s a low cost and, as far as I know, a one-of-a-kind solution for solving this growing business challenge.



