-

Here’s a BIG mobile security exposure you may be overlooking
04 Jun 2019With security, if your goal is to minimize your maximum regret, there’s a lot to be thinking about. User behaviors involving mobile devices are at the heart of some of the larger business risks, especially if you’re like the majority of businesses I see and support bring your own device (BYOD) For phones and tablets. Well, here’s something that you may have thought about in passing but haven’t done anything about…
Recently, I purchased a used cell phone off of eBay for testing purposes. When I received the phone, I realized that it had not been reset. It did have a password but no big deal – the seller had already reached out to me to provide the password so that I could get into it and do a reset. That was nice of him!
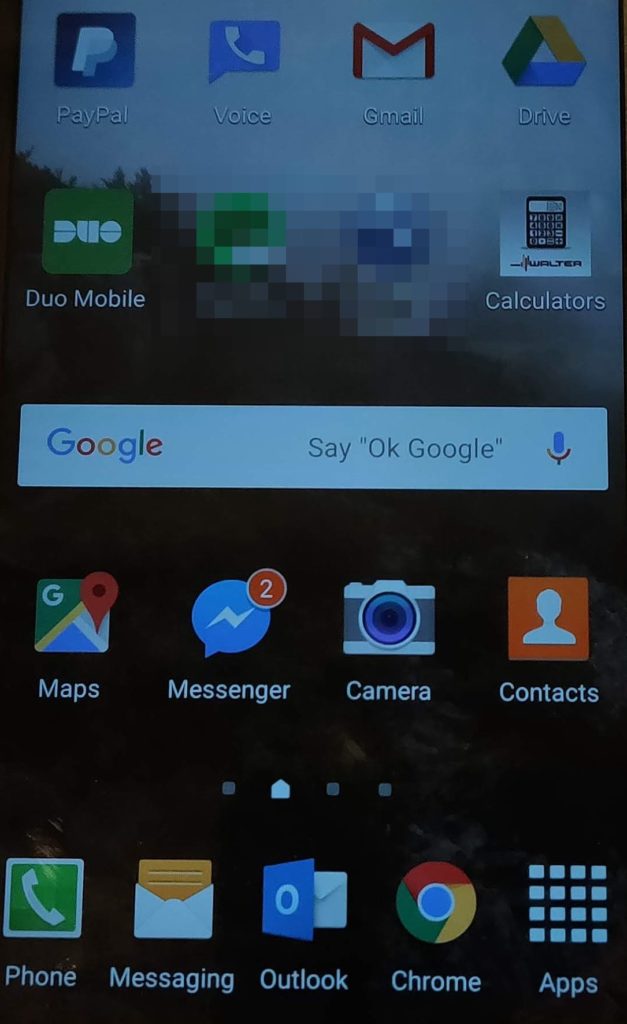
As you can see in the picture above, I had full access to what might be considered critical business apps such as Duo, Outlook, and Google Drive. PayPal and Venmo were on there as well as Dropbox and an online banking app. Of course, Facebook, Instagram, and YouTube were installed as well. Was there sensitive information on the phone? I don’t know, it was none of my business. Were the apps I mentioned accessible and, thus, exploitable? I presume but didn’t do anything with them as that’s not my line of work.
I took the photo and I’m sharing this because this very scenario is likely happening with your users and to your business. There’s nothing wrong with BYOD but you’d better make sure that your users are being trained and that expectations are properly set regarding what’s okay and what’s not. This seemingly honest mistake is unauthorized network access or a data breach in the making. Take this story and share it with your own users. Tell them what can happen if a fully-functional phone gets into the hands of a dishonest person. Talk about the long-term business consequences and the impact they can have on everyone involved. As a failsafe, provide instructions on how to do a factory reset on their devices so they know what to do when upgrading/selling down the road.



