-
27 Oct 2025
Doing the Hard Things (in security, and in life)
Everything is easy, until it's not... When you start a new relationship, everything feels easy. It’s exciting. It’s fresh. You want to impress. You like being impressed. You want to explore. Every day feels like a new adventure. But then reality sets in. The fun stuff gives way to routine, and routine takes work. You start learning nuances and dynamics. You have to show up. You have to communicate. You ...
Continue Reading... -
19 Oct 2025
Embracing Incident Response at Petit Le Mans: A Positive Outlook for Cybersecurity?
At the Petit Le Mans race this past weekend, the TV announcers couldn’t stop talking about incident responsibility. Apparently, the International Motor Sports Association (IMSA) made it clear they’re done tolerating sloppy driving. [SIDENOTE: I certainly had my fair share of that back when I raced - like this example]. The rules of racing have always been there; now IMSA says they’re finally going to enforce them. Zero tolerance. No ...
Continue Reading... -
18 Jun 2025
Revisiting an article on the security basics I wrote over two decades ago
This article is from 2004. Tell me what has changed or is outdated...Perhaps my reference to "SSL" VPNs or "anti-virus" software? ;) Information security isn’t what it’s cracked up to be these days. Sure, there are vendors out there pushing faster, better, cheaper security products. And, we have all these new fancy systems to protect our digital assets like SSL VPNs, email and wireless LAN firewalls, intellectual property “leakage” appliances ...
Continue Reading... -
15 Jun 2025
My guide for building out your incident response plan and program
Security incidents are a case of when not if. Whether it’s ransomware, information theft, denial of service - you name it, you need a structured and practical approach to incident response without the fluff and vendor noise. Is TechTarget asked me to put such a guide together a few years back...but, don't worry, it's every bit as relevant today since most things with security haven't changed in decades. Sure, the ...
Continue Reading... -
18 Mar 2020
Look for the lessons and be a leader among the COVID-19 panic
“The hardest thing to explain is the glaringly evident which everybody had decided not to see.” – Ayn Rand Interesting how the world has changed in the past couple of weeks, huh? Here in the U.S., we went from a thriving economy and living in what might be described as the best time to be alive to what seems like an abrupt halt - doom and gloom - all within a couple of ...
Continue Reading... -
07 Mar 2020
Speaking engagement for ALAS in Phoenix was a big success!
I had the opportunity to be invited to speak at the Attorney's Liability Assurance Society (ALAS) 2020 Cybersecurity Conference in Phoenix, AZ last week, and it was awesome. With a great group of 220 law firm IT leaders and general counsel professionals, I presented Beyond the Policies: Top 5 Security Findings (that I see in literally every security assessment I perform). I also served as a panelist for a lively ...
Continue Reading... -
18 Jul 2019
How does your incident response program measure up?
I've heard it said that experience is something you don't get until just after you need it. Incident response is one of those things. How do you fully prepare for something that you've never had to deal with? Well, there are ways, but you have to prepare before the going gets rough. The best thing you can do is to define what "incident" means, think through the scenarios, and create ...
Continue Reading... -
17 Sep 2018
Crashing race cars and preparing for incidents that have never happened
Just over 17 years ago, on 9/11, we witnessed what it was like dealing with something that had never occurred. I remember thinking at the time and it still rings true – it's hard to protect against something that's never happened. Little to no clues, as far as we know...massive destruction on a scale we never expected. That's the tricky thing about terrorist threats and, on a much smaller scale, ...
Continue Reading... -
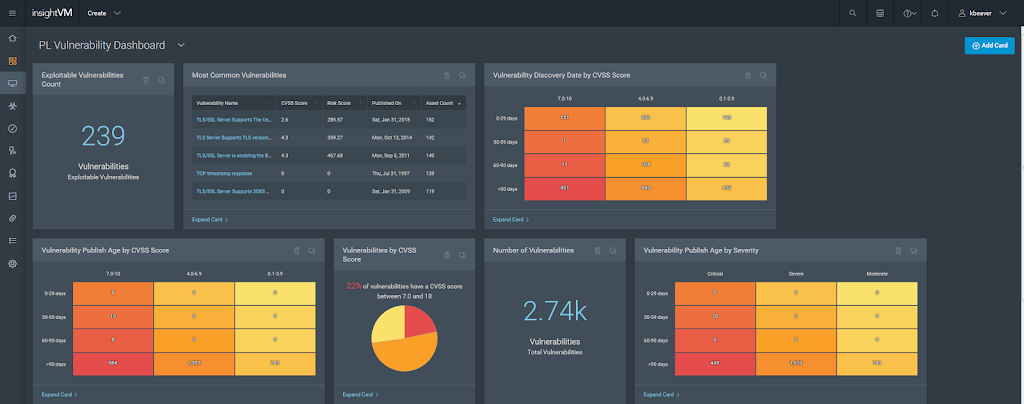
10 Aug 2017
Rapid7’s Insight platform provides focused analytics for your security program
Fairly recently, Rapid7 took their vulnerability management platform up to the next level with their analytics platform called Rapid7 Insight. It's a beneficial for an independent consultant like myself and even more useful for enterprises with IT environments of growing complexity. Rapid7 Insight is marketed as a way to bring together the Nexpose vulnerability research, Metasploit exploits, global security intelligence and exposure analytics into a single system that can help ...
Continue Reading... -
13 Apr 2017
Why SOC audit reports can be misleading, mobile app security gotchas, and more…
Here are some links to recent articles I've written regarding application security...if you take anything away from this, it's that you can't afford to take this part of your security program lightly. Dealing with vendors who want to push their SOC audit reports on you Explaining discrepancies in different security assessment reports Why DAST and SAST are necessary if software is solid from the get-go Nixing credential re-use across unrelated ...
Continue Reading...